After clicking on the 'Start Scan' button, I was treated to this view:
In the picture above, you can see the worst result is the result in the 'Security' field.
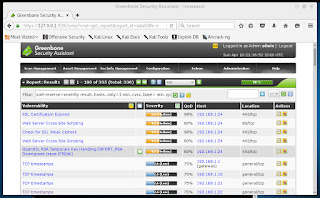
Taking a look at the report:
We can see there is one host responsible for most of the flaws, while a 'TCP timestamps' flaw is seen on four other hosts. The host with IP address 192.168.1.24 is my Cisco switch. I may go on a separate quest to see if I can squash these flaws. But, for now, they can stay. On, and TCP timestamps? One is my small router, one is a printer, one is my Mac Mini, and one is my iPhone.



No comments:
Post a Comment