Well, I like to use OpenVAS, but it is the most frustrating install I ever do, and after troubleshooting it I always think I will remember how to do it next time. And I might, but I will make a note here just in case I have to look it up again.
Here is the error after running openvas-check-setup:
Digging around a bit, I found this helpful post, and this helpful tip. But, the takeaway was I need to modify the file /etc/redis/redis.conf, adding the lines after port 0
And finally, start the redis server at the command prompt, specifying the new configuration file, with this command: redis-server /etc/redis/redis.conf
Running openvas-check-setup again, we get a whole new error:
But you can solve the rest of the error by reading the error and the suggested fix.
20160811
20160523
Password Storage in Firefox
I got to thinking about password storage in Firefox recently, and wanted to figure out if they are easy to recover. A quick search led me to to Password Fox. I tried it out, and recovered the password pretty quickly (under a minute, maybe under 10 seconds).
I started with a decent string generator, and got this for a password:
Next, i made up an account and stored the password. Finally, using Password Fox I recovered the password, as seen here:
The passwords are stored in a javascript object notation (json) file. I added a few line breaks for easy reading, but it is this:
This is all covered fairly well on Mozilla's support forum.
I started with a decent string generator, and got this for a password:
Next, i made up an account and stored the password. Finally, using Password Fox I recovered the password, as seen here:
The passwords are stored in a javascript object notation (json) file. I added a few line breaks for easy reading, but it is this:
I went back in and set a master password, and the same trick did not work. So, I recommend using this 'master password' if you're going to let Firefox store your passwords (but don't forget it).
This is all covered fairly well on Mozilla's support forum.
20160516
Add a user and hide from logon screen
This tip on how to add a user without adding them to the logon screen got me wanting to try that out on Windows 10. So, I went in there.
Here is the list of users initially with the net users command:
I can add bob with net user bob pass /add
This adds bob, and bob is now on the home screen (you can note my anonymizing edits):
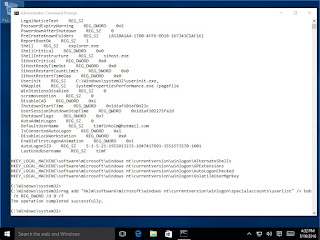
We can take a look at the registry with reg query "HKLM\software\microsoft\windows nt\currentversion\winlogon"
Next, we can add bob to the registered 'special accounts' that do not appear on the logon screen with reg add "hklm\software\microsoft\windows nt\currentversion\winlogon\specialaccounts\userlist" /v bob /t REG_DWORD /d 0 /f
Then, taking a look at the logon screen, there is no sign of bob:
And that's that. Thanks to Jose Quinones for the initial how-to.
Here is the list of users initially with the net users command:
I can add bob with net user bob pass /add
This adds bob, and bob is now on the home screen (you can note my anonymizing edits):
We can take a look at the registry with reg query "HKLM\software\microsoft\windows nt\currentversion\winlogon"
Next, we can add bob to the registered 'special accounts' that do not appear on the logon screen with reg add "hklm\software\microsoft\windows nt\currentversion\winlogon\specialaccounts\userlist" /v bob /t REG_DWORD /d 0 /f
Then, taking a look at the logon screen, there is no sign of bob:
And that's that. Thanks to Jose Quinones for the initial how-to.
20160501
A note about ARP
As you can see here, it is the nature of things that an Address Resolution Protocol (ARP) packet with an 'is-at' payload would have a destination MAC that is the same as the MAC it is describing in the packet.
We can see an example in this Wireshark capture:
That packet puts an entry in to the ARP cache like so:
To see what happens when we mix up the addresses, we can use scapy, the packet manipulation program. We can do this (at the scapy prompt):
To send this:
With only the Sender MAC inside the ARP protocol payload, we get this cache update:
So, as you can see, by changing the ARP payload, we can change which MAC is put in the cache. Also, the scapy payload was not sent in response to an ARP request, and the cache had not aged off. But, the cache was updated. With some tuning this technique could be used to accomplish ARP poisoning, and a man-in-the-middle attack.
We can see an example in this Wireshark capture:
That packet puts an entry in to the ARP cache like so:
To see what happens when we mix up the addresses, we can use scapy, the packet manipulation program. We can do this (at the scapy prompt):
To send this:
With only the Sender MAC inside the ARP protocol payload, we get this cache update:
So, as you can see, by changing the ARP payload, we can change which MAC is put in the cache. Also, the scapy payload was not sent in response to an ARP request, and the cache had not aged off. But, the cache was updated. With some tuning this technique could be used to accomplish ARP poisoning, and a man-in-the-middle attack.
20160423
Buffer Overflow - SLMail
Well, of course there is a module that will do the exploit for you, but I have joined the many people who have put together a video on how to do a buffer overflow using SLMail, Immunity Debugger, mona commands, and Kali Linux, and put the video on YouTube. Probably easier if you just watch the video, but the 'in a nutshell' version is:
1) Find a spot we can crash a program.
2) See if someone has already written a Proof of Concept for us.
3) See if it works.
4) Fix the parts that do not work.
5) Profit.
In the video we go from vulnerable service, and proof of concept, to a bind shell and a connection in msfconsole.
Hat tip to Offensive Security, whose Penetration Testing with Kali course was my first exposure to this level of detail in how a buffer overflow works. The same exercise is presented within that course, along with many others.
1) Find a spot we can crash a program.
2) See if someone has already written a Proof of Concept for us.
3) See if it works.
4) Fix the parts that do not work.
5) Profit.
In the video we go from vulnerable service, and proof of concept, to a bind shell and a connection in msfconsole.
Hat tip to Offensive Security, whose Penetration Testing with Kali course was my first exposure to this level of detail in how a buffer overflow works. The same exercise is presented within that course, along with many others.
Kali Bugs
I stumbled upon a slight error in Kali today. It was easily reproducible, so I went over to bugs.kali.org/ to report it. I had to register to report, but that was pretty painless. If you find things that you think (or know) are wrong, I encourage you to report them, too.
Oh, my thing? When I used the Applications --> Reverse Engineering --> NASM shell menu button, I got this:
So, I reported it as a broken link. Hopefully it will be fixed for all users soon.
Update: After i did a little bit of apt-get update && apt-get upgrade -y && apt-get dist-upgrade -y the menu was fixed.
Oh, my thing? When I used the Applications --> Reverse Engineering --> NASM shell menu button, I got this:
So, I reported it as a broken link. Hopefully it will be fixed for all users soon.
Update: After i did a little bit of apt-get update && apt-get upgrade -y && apt-get dist-upgrade -y the menu was fixed.
20160421
An expect script for bandit labs
If you have tried the bandit series of labs over at over the wire you have experienced trying to paste an SSH password in to the prompt, only to be unable to see what you pasted and needing to hope for the best. But, you can use an expect script like this one to log in for you, and that will save you a second here and there.
This is the script:
This is the script:
#!/usr/bin/expect
set level [lindex $argv 0]
set password [lindex $argv 1]
spawn ssh bandit$level@bandit.labs.overthewire.org
expect "password: "
send $password\r
sleep 2
send ls\r
expect "$ "
interact
You can invoke it with script_name # PASS, where script_name is whatever you name the script, # is the level number you are on, and PASS in the password for that level. If you name the script ssh_bandit, you can get to the first level (level 0) with:
ssh_bandit 0 bandit0
To look at the script line - by - line, we can see it:
1) Tells bash what program to use to run the script.
2) Sets the level variable to the first argument value.
3) Sets the password variable to the second argument value.
4) Starts an SSH session as the bandit<level#> user @ the server.
5) Waits for the password prompt.
6) Sends the password, and return.
7) Waits two seconds.
8) Sends the ls command, and a newline. (This is handy because you will often want to do a directory listing first thing.)
9) Waits for a prompt.
10) Switches to interactive mode. (Without this, typing exit to leave the SSH shell exits the bash shell.)
(Note: This may not cover the first connection for you, since the bandit server's key may not be in your known hosts, and it does not account for this variation. Feel free to improve upon it.)
(Note: This may not cover the first connection for you, since the bandit server's key may not be in your known hosts, and it does not account for this variation. Feel free to improve upon it.)
20160417
Standard Shell to Meterpreter Shell in Metasploit
TL;DR: sessions -u
As we use various exploit modules we may or may not be able to employ a meterpreter payload directly with the module. Inside the exploit module context, the show payloads command while show which payloads are available. Once a session is established without meterpreter, the sessions -u command can be used to upgrade the basic shell to a meterpreter shell. You can see the play-by-play in screenshots on YouTube, complete with narration.
Enjoy, and good luck.
As we use various exploit modules we may or may not be able to employ a meterpreter payload directly with the module. Inside the exploit module context, the show payloads command while show which payloads are available. Once a session is established without meterpreter, the sessions -u command can be used to upgrade the basic shell to a meterpreter shell. You can see the play-by-play in screenshots on YouTube, complete with narration.
Enjoy, and good luck.
20160410
OpenVAS for my home network
I have been playing with OpenVAS now and then for a few years now. I thought I would try it on my own network to see what I could find. I had set up the system before (covered here), so I simply ran openvas-feed-update and navigated over to the main page in Iceweasel, as in the following picture:
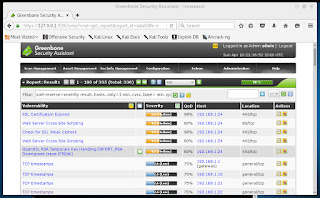
I clicked on 'Scan Management --> Reports' to see the result, as here:
In the picture above, you can see the worst result is the result in the 'Security' field.
Taking a look at the report:
We can see there is one host responsible for most of the flaws, while a 'TCP timestamps' flaw is seen on four other hosts. The host with IP address 192.168.1.24 is my Cisco switch. I may go on a separate quest to see if I can squash these flaws. But, for now, they can stay. On, and TCP timestamps? One is my small router, one is a printer, one is my Mac Mini, and one is my iPhone.
After clicking on the 'Start Scan' button, I was treated to this view:
In the picture above, you can see the worst result is the result in the 'Security' field.
Taking a look at the report:
We can see there is one host responsible for most of the flaws, while a 'TCP timestamps' flaw is seen on four other hosts. The host with IP address 192.168.1.24 is my Cisco switch. I may go on a separate quest to see if I can squash these flaws. But, for now, they can stay. On, and TCP timestamps? One is my small router, one is a printer, one is my Mac Mini, and one is my iPhone.
20160407
Sites I have Stumbled Upon
http://www.invoke-ir.com/ -- PowerShell for Incident Response
http://www.powershellempire.com/ -- PowerShell for everything offense
http://www.powershellempire.com/ -- PowerShell for everything offense
20160331
New Book Out
Dan Dieterle wrote a new book, which is an update on his old book. I did review a couple chapters for him, and he was kind enough to give a reviewer acknowledgement to me. Check it out if you would like to use a book, or maybe give one to one of your nerd friends / relations that are interested in the topic.
20160317
Windows 2008 to Debian
There comes a limit to how many virtual machines you can run on a Mac Mini. I bought a server for about $500 from savemyserver.com. It has 1.2 TB of hard drive, 48 GB RAM, and 8 cores of processor. I have not put any VMs on there yet, but did replace Windows 2008 Server that came pre-installed with Debian. From experience, I can tell you if Debian is complaining about needing some firmware to continue, you should probably figure out how to get that before you go on. I found this site to be pretty helpful when looking for individual files of firmware, rather than Debian packages which include firmware.
I'll update as I go, my dream is to use xen as my hypervisor.
I'll update as I go, my dream is to use xen as my hypervisor.
20160316
John the Mangler
When using the password cracking tool John the Ripper, I have many times used it against the LM passwords, and cracked them with a bit of time. Of course the NT passwords are (usually) just a case permutation of the LM password. So, there must be an easy way to get John to do case permutations for you. I went in to the configuration file -- /etc/john/john.conf to see if I could figure out how john word mangling rules are made. I did not, but discovered there is already a rule to get NT passwords from LM passwords. To use it, simply specify the mangling rule.
In sequence, I did this (assume the hashes are in a file called hashes) --
time john --format=LM hashes (this took about two hours)
john --format=LM --show hashes | cut -d : -f 2 | sort | tail -n 5 > word.txt
time john --format=nt --rules=NT -w:word.txt hashes (this took less than 0.1 seconds).
No video this time, comment if there's a part you don't understand, and I'll break it down.
In sequence, I did this (assume the hashes are in a file called hashes) --
time john --format=LM hashes (this took about two hours)
john --format=LM --show hashes | cut -d : -f 2 | sort | tail -n 5 > word.txt
time john --format=nt --rules=NT -w:word.txt hashes (this took less than 0.1 seconds).
No video this time, comment if there's a part you don't understand, and I'll break it down.
20160312
Beef with a Side of Kali
Many folks learn how to work with metasploit, and some folks also learn to work with BeEF. I wanted to figure out how to use them together. It took me more than 10 minutes to figure it out, so I thought I would write it down. Thanks to Sathish Arthars for his post, which was very helpful with regard to integration, and to InfoSec Institute, who had a nice write-up on getting started with BeEF.
In a nutshell, BeEF and Metasploit are meant to work together. But, they do not by default. To get them to work, you will need to change the configuration of two files. First, the file /usr/share/beef-xss/config has a pair of lines that read metasploit: enable: false, and that false will need to change to true. Secondly, change the /usr/share/beef-xss/extensions/metasploit/config.yaml file so the host and callback_host change to your actual IP address.
Finally, before starting BeEF you will need to use the load msgrpc ServerHost=<IP> Pass=<pass> command in the metasploit framework console. The IP should be the same one you put in the configuration files. Note that both the ServerHost and Pass parameters are case sensitive. Once you have the two working together, you can use a host of coordinated tactics.
I have a video of the highlights here.
In a nutshell, BeEF and Metasploit are meant to work together. But, they do not by default. To get them to work, you will need to change the configuration of two files. First, the file /usr/share/beef-xss/config has a pair of lines that read metasploit: enable: false, and that false will need to change to true. Secondly, change the /usr/share/beef-xss/extensions/metasploit/config.yaml file so the host and callback_host change to your actual IP address.
Finally, before starting BeEF you will need to use the load msgrpc ServerHost=<IP> Pass=<pass> command in the metasploit framework console. The IP should be the same one you put in the configuration files. Note that both the ServerHost and Pass parameters are case sensitive. Once you have the two working together, you can use a host of coordinated tactics.
I have a video of the highlights here.
20160306
Execute Shellcode in Firefox
Well, one of my goals for this blog is to make a note of something that took me a while to figure out, so I can look it up later, rather than relying on myself to remember. If I stumble on something you were trying to figure out, too, so much the better. I put a video together of me exploiting a Firefox browser, and then getting the hashed passwords from the computer. Here, I will put a little more explanation to keep me from talking.
The setup requires two computers. I used a Windows XP computer for my victim machine, and of course my Kali machine for the attacker. I am still using Kali 1.-something, I find it easier to find help for that one. You can get old versions of applications for testing and experimenting here. I used Firefox version 15 for this setup. The metasploit modules I used were
exploit/multi/browser/firefox_xpi_bootstrapped_addon
exploit/firefox/local/exec_shellcode
post/windows/manage/smart_migrate
post/windows/escalate/getsystem
post/windows/gather/smart_hashdump
Follow the links if you want to know more about the modules. If you want to watch the video, go here.
There is some user interaction required, I leave it to your imagination to figure out how an attacker might get a user to install a plugin or add-on. As I mentioned in the video, it is a good idea to migrate out of the Firefox process since you don't want your presence to rely on the user not closing the browser. Additionally, if you change the EXITFUNC setting to 'thread', you will not cause the browser to close when you migrate out of it or close your session. Finally, if the user is not part of the "Administrators" group, the escalation will fail, and the hashdump will fail if it is attempted without SYSTEM privileges.
The setup requires two computers. I used a Windows XP computer for my victim machine, and of course my Kali machine for the attacker. I am still using Kali 1.-something, I find it easier to find help for that one. You can get old versions of applications for testing and experimenting here. I used Firefox version 15 for this setup. The metasploit modules I used were
exploit/multi/browser/firefox_xpi_bootstrapped_addon
exploit/firefox/local/exec_shellcode
post/windows/manage/smart_migrate
post/windows/escalate/getsystem
post/windows/gather/smart_hashdump
Follow the links if you want to know more about the modules. If you want to watch the video, go here.
There is some user interaction required, I leave it to your imagination to figure out how an attacker might get a user to install a plugin or add-on. As I mentioned in the video, it is a good idea to migrate out of the Firefox process since you don't want your presence to rely on the user not closing the browser. Additionally, if you change the EXITFUNC setting to 'thread', you will not cause the browser to close when you migrate out of it or close your session. Finally, if the user is not part of the "Administrators" group, the escalation will fail, and the hashdump will fail if it is attempted without SYSTEM privileges.
20160305
Kali 2.0 Jacked My sources.list File
Well, this topic is perfectly covered at the Kali web site, but when I searched for the solution I got a lot of links pointing me to old information. So, in the hope that having enough new information out there will point your search results to the newer solution, I will post it right here.
In a nutshell, if you try to update your copy of Kali 1.* that you still like to use, you can get this error:
Err http://security.kali.org kali/updates/main amd64 Packages
404 Not Found
This is because that link does not work any more, so you get the standard HTTP 404 error.
To fix it, you will need to fix up the file that is pointing to the old repo location. Using your favorite text editor (I use vim), get your /etc/apt/sources.list file to contain this text:
/-------- START AT THE # ----------------/
/-------- STOP AFTER FREE ----------------/
In a nutshell, if you try to update your copy of Kali 1.* that you still like to use, you can get this error:
Err http://security.kali.org kali/updates/main amd64 Packages
404 Not Found
This is because that link does not work any more, so you get the standard HTTP 404 error.
To fix it, you will need to fix up the file that is pointing to the old repo location. Using your favorite text editor (I use vim), get your /etc/apt/sources.list file to contain this text:
/-------- START AT THE # ----------------/
#
# deb cdrom:[Debian GNU/Linux 7.0 _Kali_ - Official Snapshot amd64 LIVE/INSTALL Binary 20140108-17:05]/ kali contrib main non-free
#deb cdrom:[Debian GNU/Linux 7.0 _Kali_ - Official Snapshot amd64 LIVE/INSTALL Binary 20140108-17:05]/ kali contrib main non-free
deb http://old.kali.org/kali moto main non-free contrib
#deb-src http://http.kali.org/kali kali main non-free contrib
## Security updates
deb http://old.kali.org/kali-security moto/updates main contrib non-free
/-------- STOP AFTER FREE ----------------/
This is a good spot to take a snapshot if you are using a VM.
Once you save the file you can run the commands
apt-get update
apt-get upgrade
(I would restart the computer here if I got a lot of upgrades.)
apt-get dist-upgrade
20160304
Gotta Start Somewhere
Well, I sometimes wish I wrote down something I had thought about. So I thought maybe I should keep a journal, or maybe use Evernote to keep track of things. But, on the off chance that maybe somebody else might also be interested in what I was thinking about on a particular day, I decided to go with a blog. I basically have one job - Instructor at UMBC Training Centers, where I teach Information Technology and Cybersecurity - focused classes. I also have two hobbies: running and keeping up with news on the Cybersecurity front, including new tools and techniques. I am not looking to rehash the news - check The Cyber Wire if you're looking for news. But, maybe I'll post every now and then about something I found or some musings.
Today I am thinking about a tip I got from another instructor, which is there is a Capture the Flag (ctf) challenge that is always online at Over the Wire. I started playing with it, and got to level 10 or so of the 'bandit' game. Might use it, or something like it, for folks that come to learn Linux.
Today I am thinking about a tip I got from another instructor, which is there is a Capture the Flag (ctf) challenge that is always online at Over the Wire. I started playing with it, and got to level 10 or so of the 'bandit' game. Might use it, or something like it, for folks that come to learn Linux.
Subscribe to:
Comments (Atom)